Best Practices for Integrating Azure Active Directory into Ververica Platform's RBAC
When integrating Azure Active Directory (AD) into Ververica Platform's Role-based Access Control (RBAC), the authorization is working for many of our users. But for some users, it is not working. What are the best practices here?
Answer
Note: This section applies to Ververica Platform Stream Edition 2.0-2.8.
Ververica Platform supports integration with OpenID Connect (OIDC) identity providers for authentication and authorization. One common example here is Azure AD. See our documentation for an example of such a configuration. However, in a large organization, the number of groups a user is a member of can exceed the limit that Azure Active Directory will add to a token. The limit is 150 groups for a SAML token, 200 for a JWT, and 5 if the token is issued through the implicit flow. When this happens, the returned token from Azure AD does not contain the groups of the user. That is why the authorization for the user is not working. When using groups, another inconvenience is you need to configure groups' ObjectIDs, e.g., 823f758b-efc0-4f0a-96b9-1352c4c12110, in Ververica Platform. This is not intuitive and hard to maintain.
Our recommended approach is to use app roles instead of groups. This can be done in two parts.
1) Application setup in Azure AD
Assuming you have two tenants running on Ververica Platform, each in its own namespace, say team1 and team2. You can define the following roles for your app in Azure AD:
| Role | Description |
|---|---|
| team1/viewers | viewers in namespace team1 |
| team1/editors | editors in namespace team1 |
| team1/owners | owners in namespace team1 |
| team2/viewers | viewers in namespace team2 |
| team2/editors | editors in namespace team2 |
| team2/owners | owners in namespace team2 |
As we will see shortly, we will map these roles, one-to-one, to Ververica Platform roles. Now you can assign your users or groups to app roles via Azure AD Enterprise Applications. For example,
| Users | Assigned App Roles |
|---|---|
| user0 | team1/owners, team2/owners |
| user1 | team1/owners |
| team1-group | team1/editors |
| user2 | team2/viewers |
| user3 | team2/editors |
| user4 | team2/editors |
Here, user1 is assigned team1/owners as he is the lead of team1. The members of team1, represented by team1-group, are all editors. The app roles for team2 are assigned on an individual basis. user0 is assigned two roles as he works in both teams. Check the Azure documentation for details on how to create app roles and how to assign users to app roles.
Note: you can only assign groups to app roles if your Azure subscription plan allows, e.g., AZURE AD PREMIUM P2.
Note: With this approach, you will need permissions to access your application registered in your Azure AD when you add a new tenant to your Ververica Platform.
2) Setup RBAC in Ververica Platform
When a user is authenticated, the above-defined roles are passed in the ID token via the claim roles. Therefore we need to use the following Values file to instruct Ververica Platform to get the user's group membership (to assume Ververica Platform roles) from roles:
vvp:
auth:
enabled: true
oidc:
groupsClaim: roles
...
....
Now that we managed to pass Azure AD app roles to Ververica Platform, the next step is to map them to Ververica Platform roles. For this, you can add the following members to namespace team1 and team2 in Ververica Platform:
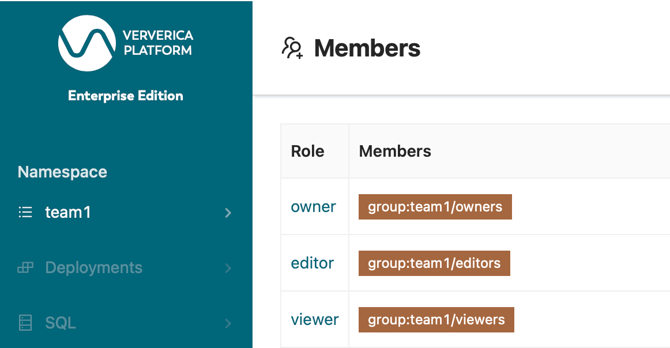

As you can see, using app roles defined in Azure AD, the RBAC configuration in Ververica Platform is simple and relatively static.
