Real-Time Fraud Detection Using Complex Event Processing
💡 What is real-time fraud detection, and how does it benefit the financial industry?
Real-time fraud detection is the immediate identification and prevention of suspicious or unauthorized activity as it happens. With real-time transaction monitoring, businesses and their customers are better protected from financial crime, payment fraud, account takeover, e-commerce fraud, and other suspicious transactions.
Real-Time Fraud Detection and Pattern Recognition
To enable faster and more informed decision-making and handle their ever-increasing data volume, businesses are embracing real-time data processing. Complex Event Processing (CEP) and Dynamic CEP are powerful tools that allow you to detect event patterns in endless streams of events, helping you pinpoint critical insights and focus on the data that truly matters, including real-time fraud detection.
In this blog post, we’ll explore how CEP is reshaping fraud prevention and anomaly detection strategies, including moving beyond batch-based systems to spot and correlate anomalies as they happen, trigger immediate interventions, and ultimately safeguard the business bottom line and brand while maintaining customers' trust. In addition, learn how Ververica’s Unified Streaming Data Platform enables continuous, stateful event processing to power fraud detection at scale. Finally, try it for yourself with several exercises available in our GitHub playground, including:
- Identifying high-value consecutive transactions (back-to-back big spends)
- Responding to multiple rapid-fire transactions
- Building location-based suspicious activity solutions
Detecting Fraud: Mission-Critical for Financial Institutions
Today, financial fraud is sophisticated, frequent, and extremely damaging. With cybercriminals constantly evolving their tactics, traditional fraud detection methods are no longer enough. The financial industry needs smarter, faster tools to keep pace, and that starts with real-time data and detection.
Are you ready to explore how real-time stream processing connects the dots before fraudsters do significant damage?

Figure One: Real-Time Fraud Detection
Real-Time Detection
The ever-increasing speed and volume of digital transactions demand an equally agile response to fraud. Real-time detection enables financial institutions to continuously monitor and assess transactions as they happen, drastically reducing the window of opportunity for criminals to exploit stolen accounts or cards. In contrast, traditional batch-based systems are slow. Analyzing transactional data happens hours or even days after the original event, by which time substantial damage has already been done.
💡 Real-time data streaming enables continuous monitoring and fast assessment of financial transactions.
Traditional vs. Real-Time Approaches
Historically, many banks rely on batch jobs that run on a set timeline to detect anomalies in transaction patterns. This delayed detection means that fraudulent transactions can slip through unchecked for a considerable period of time, and by the time a suspicious pattern is finally flagged, financial losses and damages have multiplied, as criminals have ample time to make additional unauthorized purchases or transfers.
A real-time system, on the other hand, evaluates transaction data as it flows in. Instead of waiting for large data sets to accumulate, each event is processed almost instantly. This approach offers two key benefits:
- Immediate Alerts: Suspicious transactions trigger immediate notifications, allowing fraud teams to investigate and respond right away, reducing the risk of further fraudulent activities.
- Automated Intervention: With real-time visibility, financial institutions can block cards or freeze accounts the moment they detect irregularities, containing losses before criminals exploit the window of delay inherent to batch processing.
Continuous Data Streams: Enabling Continuous Monitoring
The shift from batch-based processing to real-time analytics requires a continuous data streaming infrastructure capable of handling high-volume, high-velocity transaction data. Furthermore, the system must be able to ingest data from multiple channels, seamlessly combining data from various sources that each have the potential to generate thousands of events per second, including:
- ATMs
- Mobile banking apps
- Online payment platforms
- Point-of-sale devices
- ...and more
Complex detection logic (like identifying repeated high-value transactions or suspicious location patterns) must also be executed in-flight, with low latency, as any significant processing delay provides criminals with the time needed to complete fraudulent transactions. Also, because transaction volumes can spike unpredictably (like during holiday seasons or during major shopping events), the system must be able to scale horizontally, adding more nodes or processing resources on demand to ensure that detection capabilities keep pace.
By adopting real-time detection methodologies, financial institutions not only protect themselves and their customers more effectively but also gain critical intelligence into emerging fraud tactics. This proactive stance helps preserve trust, minimizes financial damage, and helps to meet ever-evolving regulatory and compliance expectations.
Centralizing Streams & State with Ververica’s Unified Streaming Data Platform
A core challenge in real-time processing is consolidating data from numerous disparate sources (including message queues, transactional databases, and third-party event buses) and then maintaining stateful logic on unbounded data flows. Ververica delivers this functionality by providing seamless, unified data ingestion, including integrated custom connectors and operators that funnel events from multiple channels into one pipeline.
Ververica offers real-time stream processing that enables transformations, filtering, and anomaly detection as each event arrives. Ververica also offers dynamic state management, providing tools to store and update session or user-specific information over time. As a result, Ververica can manage the complexities of continuous data ingestion, real-time analytics, and stateful computations in a single, enterprise-ready solution.
Below, Figure 2 visualizes Ververica’s real-time fraud detection pipeline, including ingestion from various financial events, consolidation of these individual transactions with the Unified Streaming Data Platform, and representation of rulesets that lead to a final response of either an alert or allow for the original transaction.
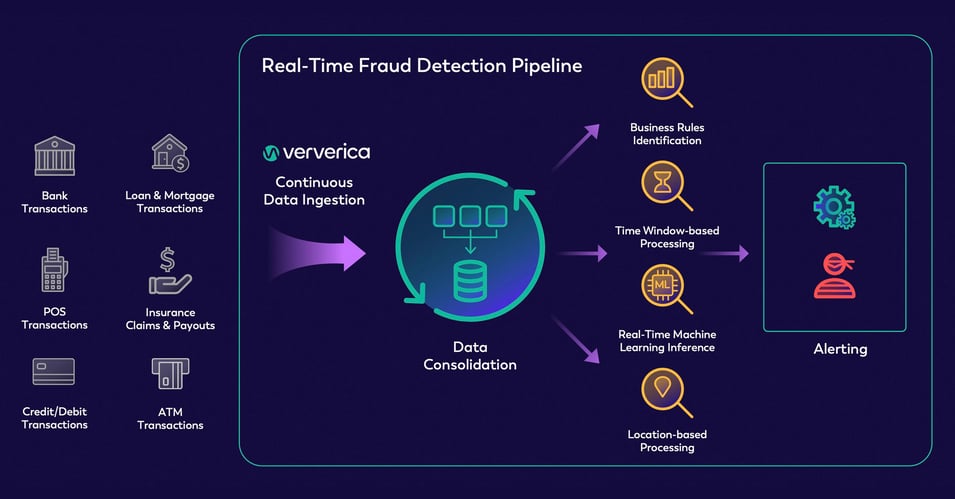
Figure Two: Ververica’s Real-Time Fraud Detection Pipeline
Both Ververica and Apache Flink® offer Complex Event Processing (CEP), a powerful tool that correlates events in real-time. The built-in CEP library makes it easy to apply CEP to streaming data, allowing businesses to define and track patterns across event streams, including detecting specific sequences and conditions that are important to their operations. As a result, teams can set up alerts, make adjustments, and trigger automated responses based on current events. As a differentiator from open-source Flink, Ververica also offers Dynamic CEP, which allows in-flight rule changes with no need to restart or experience any downtime, ideal for use cases like fraud detection, where any lag or delay in the continuous stream can have disastrous outcomes.
💡 What is Complex Event Processing?
CEP is the real-time analysis of multiple data events to identify meaningful patterns, trends, or anomalies and trigger immediate actions.
💡 What is Dynamic CEP?
The ability to adapt and modify event pattern rules based on changing data streams or conditions without pausing or restarting your data pipeline.
How Does Complex Event Processing Work?
CEP is a methodology for analyzing and matching sequences of events against predefined patterns under certain time and logical constraints. Rather than treating each event (like credit card transactions) in isolation, CEP systems observe the flow of events to detect meaningful combinations.
Figure 3 demonstrates how CEP works. Data enters via the input event streams and moves through the CEP engine, where the patterns and rules that require identification have been defined. The engine continuously monitors the input data streams, applying the defined rules. When a match is identified, CEP outputs that matching event, allowing the business to take action directly.
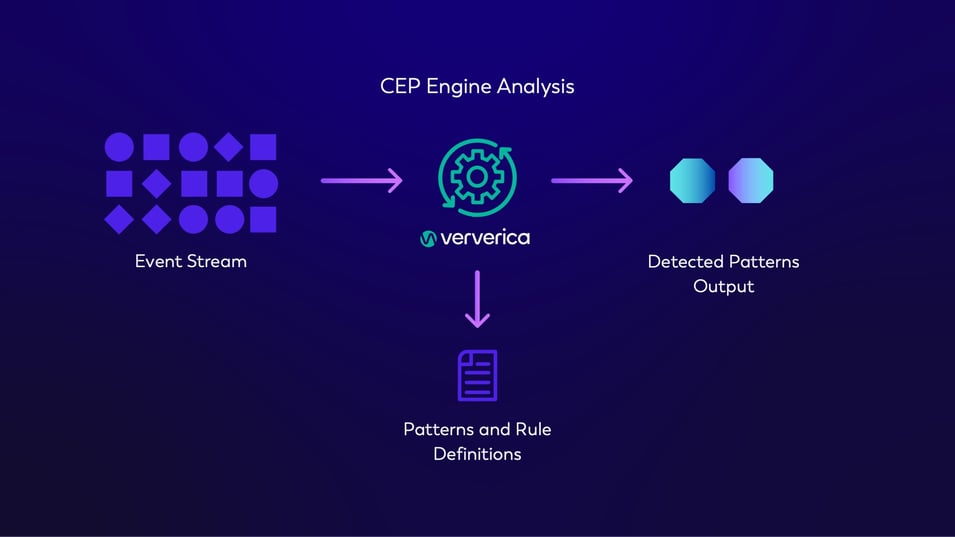
Figure Three: From Data Ingestion to Output: How the CEP Engine Works
By continuously monitoring data streams, CEP can:
- Specify Time Windows: Identify patterns that happen within seconds or minutes (e.g., 3 transactions in 10 seconds).
- Apply Flexible Conditions: Factor in transaction amounts, locations, user history, or merchant categories.
- Automate Response: Trigger real-time alerts, freeze accounts, or escalate to risk teams whenever a defined pattern is matched.
This approach provides a more holistic view of user activity, enabling proactive and immediate action when potential fraud is detected. CEP enables businesses to track critical interactions, detect risks, and initiate automated responses in real-time. The result is an environment where critical insights are identified and reported as they happen, enabling more efficient and effective operations.
Spotting Fraud in Real-Time: How Complex Event Processing (CEP) Connects the Dots
Modern financial fraud is rarely a one-off event involving only a single, isolated transaction. Instead, fraudsters create patterns of exploitation via a series of actions that are fast, subtle, seemingly unrelated, and cleverly disguised.
This is where CEP shines.
Instead of looking at transactions in isolation, CEP stitches events together in real-time, revealing suspicious behavior that single checks might miss. As a result, CEP empowers financial institutions to correlate multiple events in real-time, helping to catch suspicious activity that could otherwise go unnoticed when transactions are analyzed individually.
Complex Event Processing Applications for Fraud Detection
Now, let’s create and test a few real-world fraud scenarios. Below are three common challenges that financial institutions face that illustrate how CEP correlates events together and can raise the alarm more effectively than single-event checks. Find sample implementations of the fraud patterns below in this GitHub repo. And, it includes a data generator to test it out!
💻 Try it!
Find sample implementations of the fraud patterns below in this GitHub repo, including a data generator to test them out.
Exercise One: High-Value Consecutive Transactions (Back-to-Back Big Spends)
- Scenario: A stolen credit card gets swiped for two big purchases, each over $900, within just 30 seconds.
- Why it’s suspicious: While a legitimate user might splurge on pricey back-to-back purchases, multiple expensive purchases in quick succession are also a classic move for fraudsters trying to max out a stolen card before it’s shut down.
- How CEP helps: CEP connects the dots quickly, with continuous monitoring and pattern recognition that helps identify a possible account takeover, instantly flagging these events as suspicious. That alert prompts extra bank security checks or automatically freezes the card, stopping the financial crime before it spirals out of control.

Figure Four: High Value Consecutive Transactions
Exercise Two: Multiple Rapid-Fire Transactions
- Scenario: Within a very short timeline, multiple small transactions from different online stores occur from a single account.
- Real-Life Context: While a person might have a good reason to make several small purchases from different online stores within a very short time period, the rapid frequency of the purchases is unusual and points to another classic tactic used by fraudsters. Testing out stolen cards by exploiting smaller transaction thresholds allows potential account takeover to go unnoticed, as no individual event is an obvious suspicious transaction when inspected independently from one another.
- How CEP Helps: CEP continuously monitors for bursts of activity in short time windows (for example, three or more transactions in 10 seconds). By defining a specific time window and looking for multiple consecutive events, CEP alerts the bank anytime it detects these bursts of activity that might be an anomaly. As soon as this pattern appears, the system flags it, and the bank can then temporarily block the card and ask the real account owner whether the recent transactions are real or a financial crime.

Figure Five: Multiple Rapid-Fire Transactions
Exercise Three: Location-Based Suspicious Activity (The “Impossible Travel” Trick)
- Scenario: A credit card is used in Berlin, and then again in London less than 20 minutes later.
- Real-Life Context: Even with modern travel, covering that geographical distance in mere minutes is completely impossible. This type of activity indicates card cloning, account takeover, or account compromise, including possible card theft or illicit account sharing.
- How CEP Helps: CEP calculates both the distance and elapsed time between transactions to catch these “impossible travel” events. If the travel time doesn’t add up, it immediately flags the activity. Using real-time alerts that prompt the bank to initiate step-up authentication or block the account until the user verifies their location, the bank can engage in better fraud prevention and reduce financial crimes.
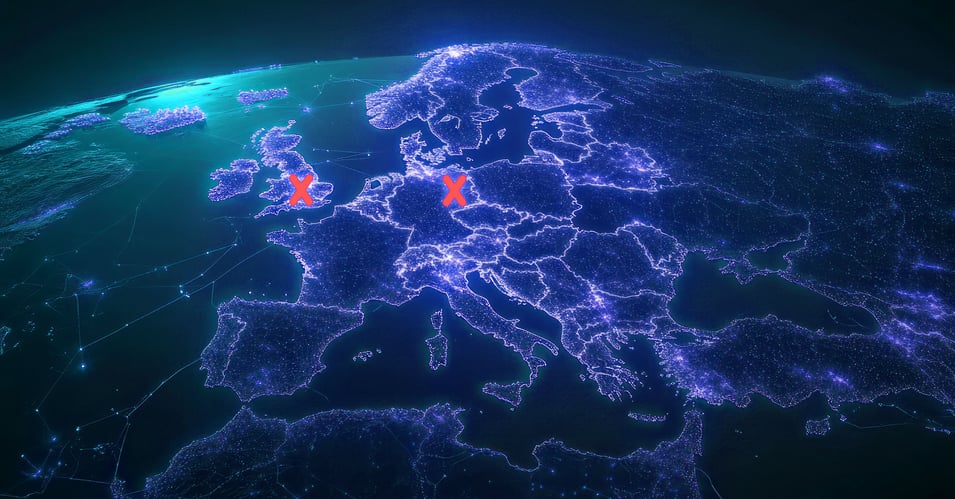
Location-Based Suspicious Activity
Conclusion: Correlating Multiple Events
Fraud detection systems are a must-have for financial institutions (fraud trend predictions for 2025 show an increase in both fraud activity and pressure regarding how a company should respond to protect customers), and real-time capabilities are the difference in limiting losses and protecting customers. Modern fraud is rarely the result of a single suspicious event, instead, it’s a sequence of subtle, fast-moving actions that only make sense when viewed in context. CEP excels at identifying these patterns, helping to expose risks that would otherwise remain hidden. Rather than reacting to individual anomalies, CEP enables financial institutions to act on meaningful correlations in real time, whether that’s detecting a rapid burst of high-value purchases or spotting location shifts that don’t align with usual user behavior.
Acting like a smart security camera for your data, CEP is always on, always learning, and always ready to act, helping to connect the dots across time, geography, and transaction types, and empowering financial institutions to detect and stop fraudulent behavior in real time.
Ultimately, financial institutions gain a future-proof fraud detection solution that is scalable, adaptive, and resilient. With Ververica’s Unified Streaming Data Platform, data teams can centralize data ingestion, stateful processing, and pattern detection in a singular, robust solution. With the ability to correlate complex behavior patterns and trigger instant responses, Ververica helps organizations stay one step ahead of evolving threats, safeguard customer trust, and meet the growing demands of a real-time digital economy.
More Resources
Learn more about the importance of real-time fraud detection in: “Outrun Fraudsters with Agentic AI,” where we discuss two transformative technologies, Agentic AI and stream processing, and how, when combined, they form a powerful solution for combating fraud effectively.
Read more about real-world CEP use cases in “Real-Time Insights for Airlines with Complex Event Processing”. (Also includes GitHub exercises to try for yourself!)
Watch the video: “Understanding Complex Event Processing with Applications in E-Commerce Platforms” for more examples of how CEP correlates data into actionable insight, including:
- Cross-sell and upsell opportunities
- High-value card abandonment detection
- Purchase intent scoring
- Price sensitivity detection
- Churn prediction
Try out CEP for yourself! Create a real-time streaming application.
Ready to learn more about Ververica’s Unified Streaming Data Platform?
You may also like

Zero Trust Theater and Why Most Streaming Platforms Are Pretenders
Most streaming platforms fall short of true Zero Trust and operational re...

No False Trade-Offs: Introducing Ververica Bring Your Own Cloud for Microsoft Azure
Ververica introduces BYOC for Azure, delivering enterprise-grade streamin...

Data Sovereignty Is Existential Most Platforms Treat It Like a Feature
DORA and NIS2 demand provable data sovereignty. Most streaming platforms ...

Dual Pipelines Are Done. Ververica Unifies Batch and Streaming.
Ververica unifies batch and streaming data execution, eliminating pipelin...














